
We rely closely on our networks for enterprise continuity. As know-how evolves, we will achieve this rather more. On the similar time, elevated complexity makes it difficult to maintain monitor of every thing. Reaching and sustaining community visibility generally appears like chasing the carrot on the finish of the stick.
Desk of Contents:
What is Network Visibility?
Why is Network Visibility Important?
Challenges to Network Visibility
Network Visibility Best Practices
Conclusion
When discussing visualizing the community, we do not imply staring endlessly at inexperienced characters scrolling vertically. We’re speaking about understanding what’s taking place in your community and who’s utilizing it.
This information will clarify learn how to obtain community visibility in your group.
What’s Community Visibility?
Community visibility observes your network infrastructure from finish to finish. It appears to be like in any respect related elements, together with linked gadgets, digital environments, functions, and finish customers, and the info that flows between these sources.
Visibility does not care about utilizing CRM vs CDP to gather buyer information. It is solely involved with monitoring and controlling the place that information flows.
The intention is to know each a part of your community and what “regular exercise” appears to be like like so you can also make effectivity enhancements whereas safeguarding in opposition to safety threats.
Why is Community Visibility Essential?

Reaching community visibility takes an enormous, coordinated effort, however it’s well worth the funding.
Day by day enterprise actions are shifting additional into digital areas, so that you’re on the mercy of your community and its infrastructure. Why would not you need a method to monitor community efficiency and incidence?
Let’s dig deeper into a few of the causes to prioritize community visibility.
Cybersecurity
In accordance with IBM, the worldwide common information breach value rose to $4.88 million in 2024.
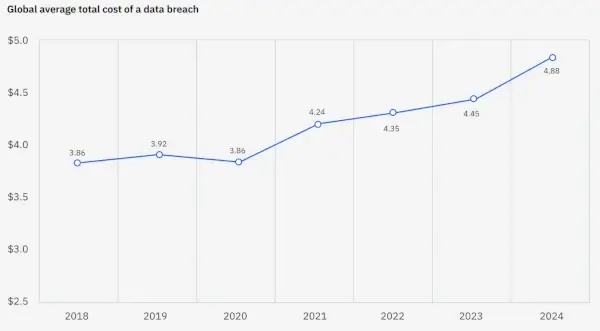
Breaches are considered one of some ways hackers can injury your community (and enterprise). They will additionally break web sites, swap servers, and take your utility providers down.
Better community visibility permits you to be proactive by observing information flows in actual time and taking motion as quickly as you determine a weak point.
Risk Identification
Malware and different threats will try and penetrate your community. If and once they do, community visibility instruments rapidly determine the problem. Figuring out what you are coping with is half of the battle.
Determine Blind Spots
Regardless of finest efforts, each community has hidden vulnerabilities. Community monitoring helps you compile historic information and set up baselines for what’s anticipated. Irregular tendencies and patterns spotlight areas in danger for intrusion.
Troubleshooting
Discovering the basis explanation for issues is simpler once you’re already observing them as they happen. You may attain options quicker, mitigate threats, and reduce network or website downtime. Which means you scale back losses, keep enterprise continuity, and preserve clients comfortable.
Enhancing Community Efficiency
Community visibility means higher visibility of the circulation of knowledge vertically and laterally. This produces insights for optimizing bandwidth and dealing with visitors to get rid of bottlenecks and enhance end-user responsiveness.
Compliance
Knowledge privateness and safety legal guidelines demand documentation and traceability for delicate buyer information. In the event you’re monitoring your community, you will have instantaneous entry to community information to account for what info was uncovered and when.
Higher Planning
Monitoring and analyzing community information offers perception into the well being of the general community. By getting forward of issues similar to growing old and legacy enterprise apps or overloaded CICS mainframes, you may then change {hardware} and software program earlier than it is too late and keep enterprise continuity.
Challenges to Community Visibility
Full community visibility requires dealing with many variables plus swathes of knowledge. So, it is vital to pay attention to what challenges that you must navigate.
- Distant entry. Owl Labs experiences that 38% of staff are hybrid or absolutely distant at present. Whereas distant work has many advantages for workers and companies, it may make visibility difficult. Customers usually hook up with enterprise techniques on Digital Personal Networks (VPNs) that provide encryption however stop normal monitoring and restrict visitors visibility.
- Community complexity. As extra community assets shift to the cloud, the necessity for cloud security reduces visibility. Web of Issues (IoT) gadgets use edge computing, disconnecting information out of your community.
- Software limitations. Every software has its limitations and blind spots in information assortment and evaluation. It’s essential to use the best mix of instruments to cowl your bases.
- Knowledge encryption. SSL and different encryption strategies are normal observe. Whereas this protects information, it comes on the expense of decrease visibility. Hackers will use the identical sorts of visitors encryption to cover their actions in your community.
7 Community Visibility Finest Practices
If you wish to obtain full community visibility from day one till lengthy into the long run, comply with these pointers.
1. Construct Sustainable, Dependable Knowledge Assortment

Complete evaluation requires you to parse by big volumes of visitors and circulation information. You may’t all the time parse each single byte of knowledge. As a substitute, you want constant indicators of community efficiency and well being.
Optimize Packet Entry
The smallest bytes of transferred information for evaluation are generally known as packets. It’s important to seize packets successfully, in any other case, you will develop blind spots. Work with IT specialists to entry and choose the very best packet varieties for monitoring.
Selecting dependable community slices will allow you to troubleshoot points and flag anomalies. Use network monitoring tools that may scale as your visitors grows.
Embrace Digital Infrastructure
Right now, accommodating cloud and cell networks and the gadgets that hook up with them is significant. Nonetheless, digital environments like cloud-based providers, digital machines (VMs), and software-defined networks (SDNs) obscure visitors.
To counteract this, visibility instruments constructed for cloud-based environments needs to be applied. These join the bodily and digital layers, monitoring information because it strikes from one digital information middle to a different for higher visibility.
Deploy Community TAP and SPAN Port Applied sciences
Check entry factors (TAPs) present steady entry to visitors for passive monitoring. Switched port analyzers (SPANs) are used for port mirroring, the place packets are copied and despatched to your information hubs.
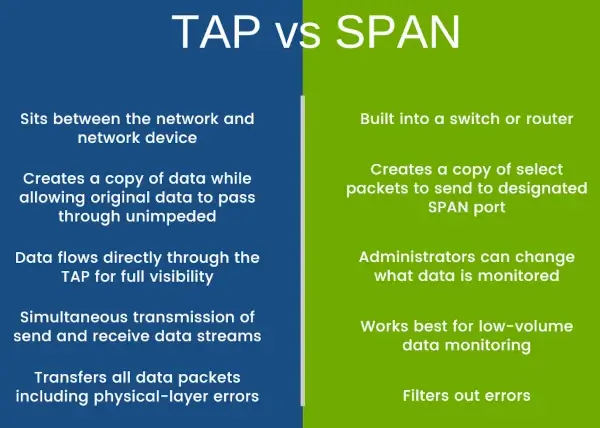
TAPs are less complicated to implement, however each introduces a risk entry level. SPANs are extra versatile than TAPs however are restricted within the quantity of knowledge they’ll monitor. Think about using each for better adaptability to altering community complexities.
2. Monitor All Community Layers
Your community has a number of layers, every of which presents attainable points. True visibility incorporates a monitoring course of on each layer.
In accordance with the Open Systems Interconnection (OSI) model, there are seven layers in a community:
- Bodily layer. {The electrical} and optical pulses of knowledge transmission to the bodily system.
- Knowledge hyperlink layer. Knowledge travels node-to-node and is verified, error-corrected, and packaged.
- Community layer. Receives information and progress towards goal locations.
- Transport layer. Protocols similar to TCP regulate the switch of knowledge packets.
- Session layer. Manages connection and exchanges between two gadgets.
- Presentation layer. Knowledge is translated or transformed into info appropriate with the applying.
- Utility layer. The place the end-user interacts, visitors contains utilization and clickstream data analysis.
Determine related layers and elements in your community and set up monitoring protocols for every. For instance, IP monitoring is crucial for monitoring the community layer. Whereas, bodily layers usually require sensors and in-person testing.
3. Automate Contextual Alerts
Community visibility does not assist a lot if you happen to’re not alerted to potential issues and visitors anomalies. It is also not all the time helpful in your crew to get a easy notification that one thing within the community is down.
Individuals need actionable info. What’s taking place and why? The place is the problem positioned? What is the really useful plan of action?
Customise monitoring and risk evaluation instruments to ship contextual notifications. Ship these to applicable crew members, giving them a head begin to fixing community safety and efficiency points.
4. Use Community Monitoring Options
One of the best ways to construct visibility is with community monitoring providers that automate the method. Many distributors supply varied information monitoring choices.
WebSitePulse offers monitoring for:
- Databases
- Distant providers
- Net servers
- VoIP servers
- E mail servers
- DNS servers
- Community uptime
Utilizing providers like this places community visibility within the arms of the specialists, guaranteeing full visibility and proactive measures for an added layer of safety. It screens your website 24/7, sending instant alerts in case of error detection to cut back the danger of misplaced income from community downtime.
5. Prioritize Utility Monitoring
For many of your crew, significantly in the event that they’re hybrid or distant, functions assist get the job finished. You wish to monitor utility efficiency and guarantee folks get the required productiveness increase.
Utility efficiency monitoring (APM) instruments monitor the end-user expertise, efficiency metrics, and availability. In brief, they guarantee your crew can use vital apps for the required jobs. Working apps additionally imply happier staff.
6. Implement Encrypted Site visitors Evaluation
Site visitors encryption is crucial for cybersecurity and compliance. Encrypted Site visitors Evaluation (ETA) instruments similar to GREYCORTEX Mendel monitor encrypted visitors with out decrypting it, sustaining each safety and privateness.
ETA makes use of metadata, visitors patterns, and machine studying to detect anomalies or threats hidden inside encrypted flows.
Different techniques for rising the visibility of encrypted visitors embody:
- Allow and Monitor SSL/TLS decryption. Selectively decrypt visitors to examine contents.
- Set up packet circulation switches. Ship a number of decrypted copies to completely different evaluation instruments.
- Use proxy-based structure. Decrypt for evaluation, then re-encrypt earlier than shifting information alongside.
7. Leverage Distant Community Monitoring
Distant entry permits your small business to work extra flexibly and keep aggressive. Whereas it hinders visibility, there are a number of workarounds you may implement.
Use the next to leverage distant community monitoring
- Cloud-based community monitoring instruments. Present real-time entry to community information throughout the atmosphere.
- Probes and sensors. Deployed remotely to seize visitors information and ship it to centralized monitoring.
- VPN and SD-WAN monitoring. Monitor visitors for distant staff connecting to your community.
Safe Your Enterprise With Better Community Visibility
Your group will solely get so far as your community techniques can take you. Do not depart issues as much as probability, and solely react when one thing breaks.
Enhance your community visibility with risk identification instruments and monitoring providers. It will defend your community and the delicate info of your staff and clients.
Higher visibility additionally means higher management of knowledge flows for better community efficiency. Do not put it off till you lose the community. Begin constructing a visibility technique at present!








