Totally different types of cyber assaults are prevalent as of late and the sophistication of assault strategies has reached new ranges the place attackers are now not restricted to faux web sites, messages or emails however steal knowledge and safety from social media platforms. System failure can be being addressed. Social engineering assaults are on the rise, forcing victims to reveal confidential, private or delicate data after which utilizing it for monetary achieve or to perpetrate cybercrimes.
At present we take a look at two cyber assault methods in additional element: Forgery And Spamhow these assaults are carried out, how you can determine such assaults, steps that may be taken to keep away from being a sufferer of such assaults and many others.
What’s Phishing?
Cybercriminals commit fraud and procure confidential data resembling passwords, or details about bank cards or different banking particulars, which might result in monetary loss. Social engineering methods resembling tricking official customers to acquire crucial data are on the rise. A cybercriminal or attacker normally poses as an individual or a trusted enterprise in an official communication utilizing electronic mail or on the spot message, social networks, and even telephone calls.
Associated: Spearfishing vs Phishing
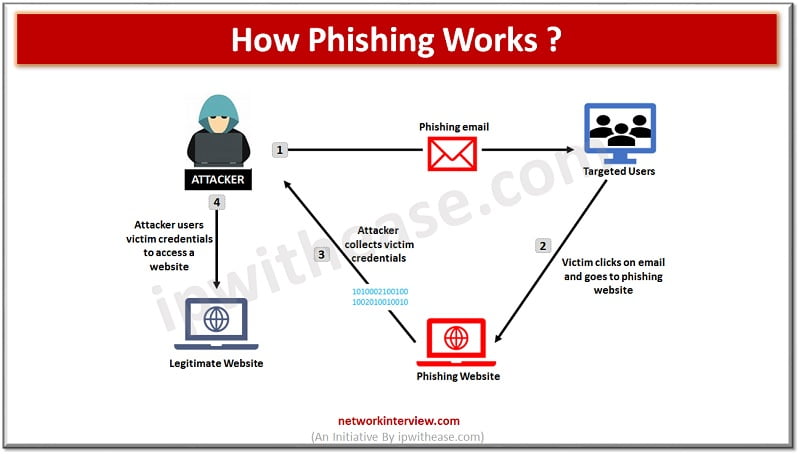
Such emails normally include a malicious hyperlink that, by clicking on it, methods customers into believing they’re on a trusted web site and supplies the requested data, which falls into the fingers of the spammer. .
- Often known as SMS-based phishing assault. Smiling It’s one by which a person receives a textual content message to go to a malicious hyperlink or
- Oh vishing One kind of phishing assault is the place a person receives a name from a financial institution or different monetary establishment asking for private particulars that the attacker can use to steal cash.
What’s spam?
Spam is nothing however flooding mailboxes or programs with unsolicited messages from unknown senders that you haven’t requested or desired. The character of most spam mail is to promote a services or products. Spammers purchase databases that include 1000’s of electronic mail addresses and infrequently conceal the origin of the message or sender data with the intent of damaging or choking the system.
Spam can be utilized by hackers to create issues for community directors, resembling flooding programs, taxed bandwidth, undesirable use of space for storing, and many others.
The right way to keep away from phishing and spam?
- Don’t click on on unsolicited emails or hyperlinks.
- Don’t enter your private delicate data on unsecured websites if the location’s URL doesn’t begin. HTTPS And the lock image doesn’t file any delicate data or obtain any recordsdata from such websites.
- Rotate your passwords frequently and enabling multi-factor authentication is an effective technique to hold passwords safe.
- Be sure that your system has the newest safety patches and updates put in.
Comparability Desk: Phishing vs Spam
The desk under summarizes the variations between the 2 cyber assault applied sciences:
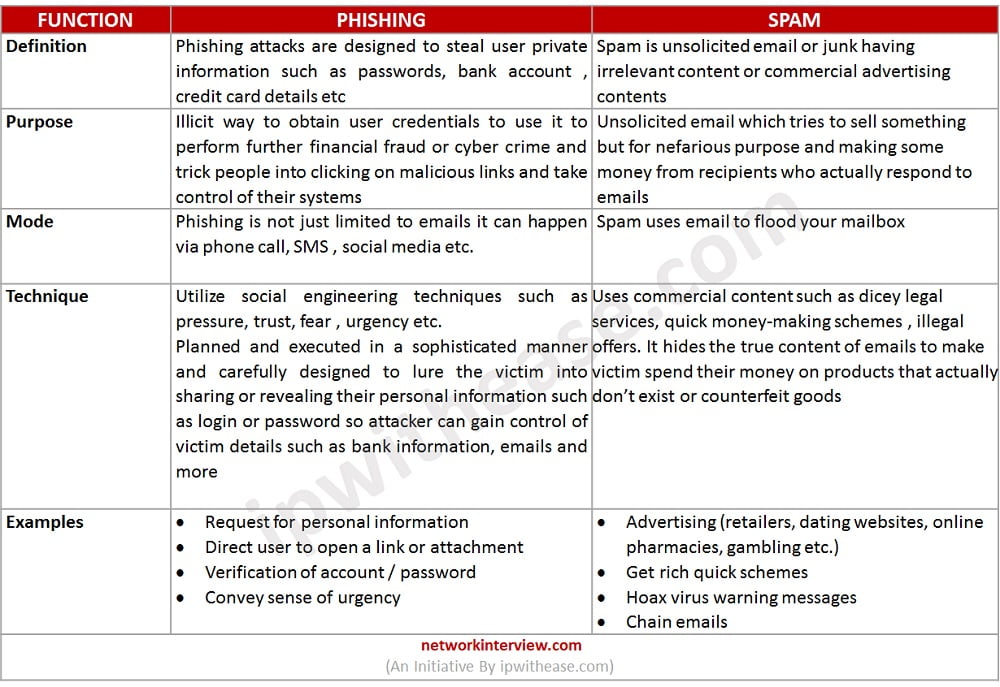
Obtain the comparability desk right here: Phishing vs. Spam
Proceed studying:
What’s spoofing? Detailed description
Prime 10 Cybersecurity Traits







