Subdomains are an integral a part of a web site’s infrastructure. They supply further performance to an online software, reminiscent of APIs, admin portals, and staging environments.
As an moral hacker, discovering subdomains is a crucial step in studying the assault floor of a goal. In contrast to the principle area, subdomains is probably not properly protected. To allow them to be a wonderful entry level for safety auditing or bug bounty applications.
On this article, I’ll let you know methods to discover subdomains utilizing a number of strategies. We are going to use tesla.com as our instance in subdomain analysis.
Word: tesla.com is a part of the bug bounty applications, so we’ve got permission to scan it for subdomains. If you’re doing this in one other net software, be sure to have permission.
Crt.sh
One of many best methods to start out is to examine the Certificates Transparency (CT) logs utilizing crt.sh. This web site data each SSL/TLS certificates issued for a website, together with subdomains.
To seek for Tesla subdomains, go to crt.sh and enter %.tesla.com Because the query. gave % Acts as a wildcard to match any subdomain.
Let’s have a look at the outcomes:
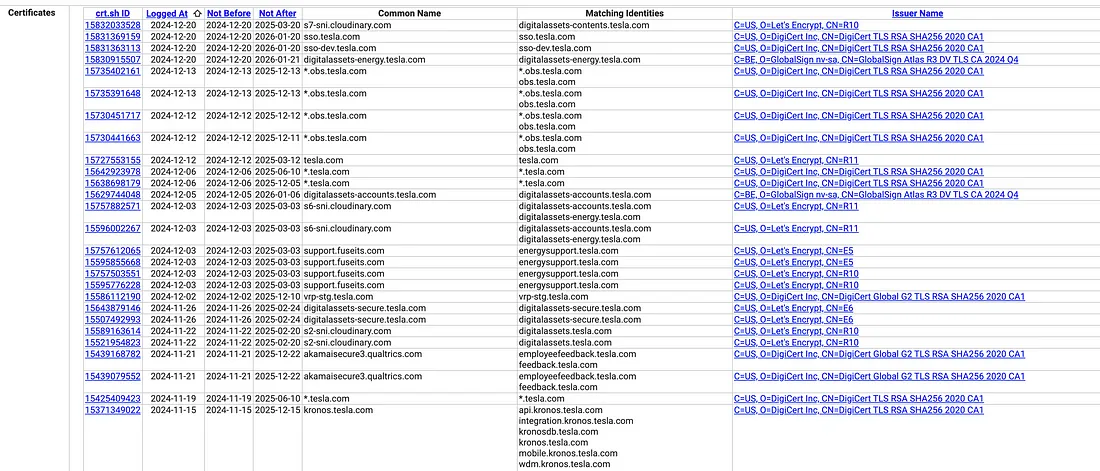
We will see many attention-grabbing subdomains listed within the outcomes. These subdomains belong to totally different elements of Tesla’s infrastructure.
For instance, store.tesla.com Whereas there’s a chance for his or her on-line retailer api.tesla.com Can host an software programming interface.
to make use of crt.sh is passive, which means it doesn’t work together with the goal, making it each protected and stealthy.
Word that crt.sh will solely show subdomains which have legitimate certificates. If a subdomain makes use of a self-signed certificates or doesn’t use SSL/TLS in any respect, it might not seem in these logs. Regardless of this limitation, crt.sh is a quick and environment friendly start line for subdomain enumeration.
Sub-list 3r
Sublist3r is an open supply device for automating the seek for subdomains. That is useful in each safety assessments and basic reconnaissance.
By utilizing a number of serps (like Google, Bing, Yahoo, and extra) Sublist3r finds subdomains that may in any other case be hidden.
Sublist3r’s command line interface is simple to make use of – you give it a website, and Sublist3r does the work.
Due to its open supply nature, it’s actively maintained and improved by the safety neighborhood.
Sublist3r just isn’t already put in on Kali, so let’s go forward and set up it. First, clone the repository and set up the conditions:
git clone https://github.com/aboul3la/Sublist3r.git
cd Sublist3r
sudo pip set up -r necessities.txt
Now we’re prepared to make use of the sublist3r device. Here is the syntax for utilizing sublist 3r:
python sublist3r.py -d tesla.com
After a couple of minutes, Sublist3r will return a listing of found subdomains. gave -d The flag tells sublist3r that the area to make use of is tesla.com.
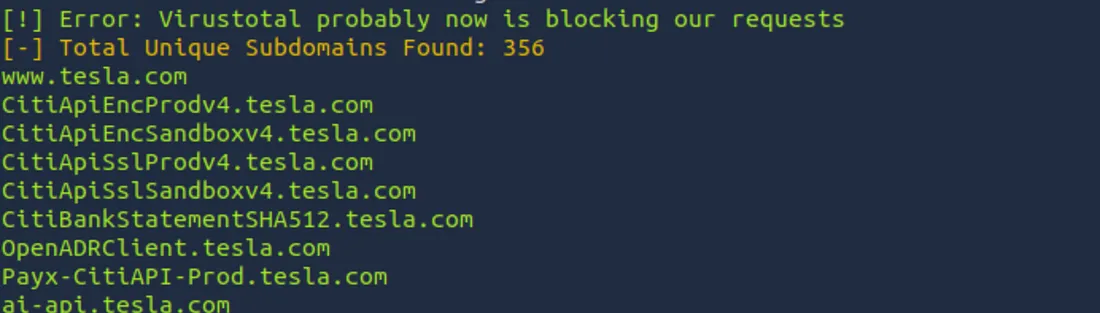
You’ll be able to see that sublist3r discovered over 300 subdomains of tesla.com. Sublist3r is an effective way to jumpstart the recon course of, particularly if you wish to automate the gathering of subdomains with out putting in a number of separate instruments.
Word that Sublist3r depends on the APIs of those serps and different information sources. So it may well generally miss subdomains that aren’t crawled or listed.
Google Dorking
Google dorking (generally known as “Google hacking”) refers back to the apply of utilizing specialised search queries on Google. These operators assist find hidden info, delicate information, or different assets that may in any other case be tough to find.
Widespread operators embody web site:, inurl:, filetype:and intitle:amongst many others. Let’s begin with web site: Operator:
web site:*.tesla.com
This question searches for any subdomain. tesla.com. Listed below are some search outcomes.
To dig deeper, strive combining web site: with different operators. For instance, we will use inurl To seek out URLs containing the operator phrase admin with the key phrase ‘admin’.
web site:*.tesla.com inurl:admi
Utilizing these operators (often known as Google dorks), you’ll be able to filter search outcomes to seek out particular file varieties, directories, and even personal info that could be unintentionally returned. can seem on the Web.
Dorking can generate a number of information, so you could have to filter your search fastidiously to keep away from a flood of irrelevant info.
Here’s a full tutorial on Google Dorking.
Fuzzy with GoBuster
Now what if a goal’s subdomains aren’t listed anyplace on the Web? We fuzz for him.
Fuzzing is to power potential subdomain names by attempting combos of wordlists. The wordlist is a listing of phrases that we are going to use with the fuzzing device to see if a subdomain exists.
A subdomain glossary could embody phrases reminiscent of:
ftp
root
admin
portal
api
Instruments like Gobster and Fiff can use wordlists to examine if these subdomains exist. Here’s a pattern subdomain glossary.
How does Gobster work?
Gobster is a quick device for locating hidden URLs, information and directories inside web sites.
Ffuf is a wonderful net fuzzer, however Gobuster is a sooner and extra versatile various. Gobster has help for extensions with which we will prolong its capabilities.
Gobster can even scale utilizing a number of threads and carry out parallel scans to hurry up outcomes.
Gobster comes pre-installed in Kali Linux. Let’s run the next command to seek out the subdomains. You’ll find wordlists underneath /usr/share/wordlists/SecLists in Kali Linux.
gobuster dns -d tesla.com -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
The above command checks every phrase within the glossary to see if it resolves to a legitimate subdomain. Here’s a pattern output:
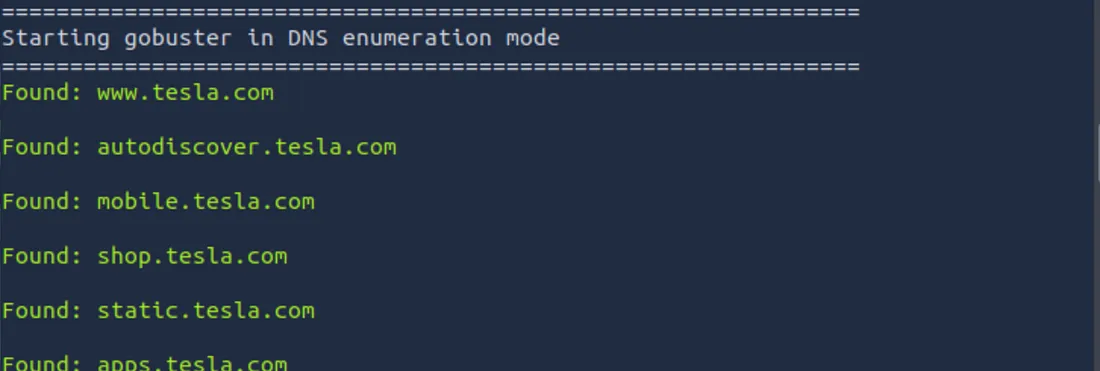
Gobster outcomes present legitimate subdomains, together with some that won’t seem in public databases, e.g staging.tesla.com or dev.tesla.com.
Fuzzing must be mixed with different strategies as a result of the outcomes are solely nearly as good because the checklist of phrases. For instance, prod-version-2.tesla.com could also be a subdomain that is probably not a part of the wordlist.
Different strategies of subdomain discovery
DNS zone switch
Though uncommon, misconfigured DNS servers can enable zone transfers, which expose all subdomains without delay. You’ll be able to check utilizing this. dig:
dig axfr @ns1.tesla.com tesla.com
If the server is correctly secured, it won’t enable zone transfers. But when it is misconfigured, you’ll be able to expose each subdomain Tesla makes use of.
On-line instruments
Web sites reminiscent of SecurityTrails, Shodan, and Censys accumulate subdomain information. These instruments present a centralized view of publicly accessible info.
Inspecting JavaScript information
Subdomains typically seem in a web site’s JavaScript information. By reviewing Tesla’s web site, you could discover references to API endpoints or different subdomains.
Submit subdomain discovery
Upon getting a listing of subdomains, we will examine them additional. We could uncover sign-in portals, growth pages, or API endpoints.
Moral hackers usually use port scanning and repair enumeration instruments reminiscent of Nmap and Nikto to seek out open ports and operating companies on every subdomain. Figuring out outdated software program, insecure protocols, or default credentials is usually the following essential step, as these are widespread weak factors in any setting.
Subdomains typically present us the broader infrastructure of a web site if they’re left unprotected.
The end result
Subdomain discovery is a crucial ability for moral hackers. It helps us perceive the entire image of the online software. The extra we all know, the higher entry factors to entry.
Earlier than utilizing these strategies, at all times be sure to have the right permissions. Subdomain discovery helps safety audits by exposing hidden property and serving to organizations defend themselves from potential threats.
For extra sensible classes on cybersecurity, be a part of us. Weekly e-newsletter. If you wish to apply these subdomain discovery strategies by means of a hands-on lab, be a part of us. Hackers Hub.







